Achieving SOC 2 compliance isn’t just about checking off a list of security measures—it’s about demonstrating that your organization has a thorough, well-documented process for securing sensitive data. Doing so builds trust in the way your organization handles data security and integrity.
A key part of the preparation for a SOC 2 audit process is writing well-formed control descriptions. These descriptions specifically define how your organization ensures security, availability, processing integrity, confidentiality, and privacy. However, they must be structured in a way that is both clear and verifiable by auditors.
What is a Control Description?
A control description explains the specific process or procedure your organization follows to meet SOC 2 Trust Services Criteria. Rather than a rigid checklist of requirements, SOC 2 controls are adaptable, allowing businesses to tailor them to their unique risks and operational structure. Well-formed control descriptions provide the necessary level of detail to explain what the control is, how it functions, and who is responsible for implementing it.
Key elements of a strong control description include:
- Defining who is responsible for the control’s execution (a team, department, or role rather than a specific individual).
- The process or action is taken to ensure compliance with the trust services criteria.
- How the process is implemented and monitored to ensure effectiveness.
- The frequency of programmatic activities (i.e. monthly, quarterly, bi-annually, annually, etc.)
For example, a poorly written control might state, “The CTO approves all new user access requests.” A stronger control would be something along the lines of “A designated IT team member reviews and approves new user access requests based on authorization from department heads before provisioning credentials.” The latter example provides more flexibility and ensures alignment with audit requirements.
How Does It Differ From a System Description?
A system description is a narrative that outlines an organization’s overall approach to security and compliance. While it includes details about infrastructure, policies, and processes, it does not provide the granular level of detail found in individual control descriptions.
The system description should align with the controls being tested in a SOC 2 audit. If the system description states that access to critical systems is controlled, then there should be control descriptions specifying how access is reviewed, authorized, and revoked. A mismatch between the two can create confusion during an audit and potentially hinder certification.
How Will a SOC 2 Auditor Judge Internal Controls?
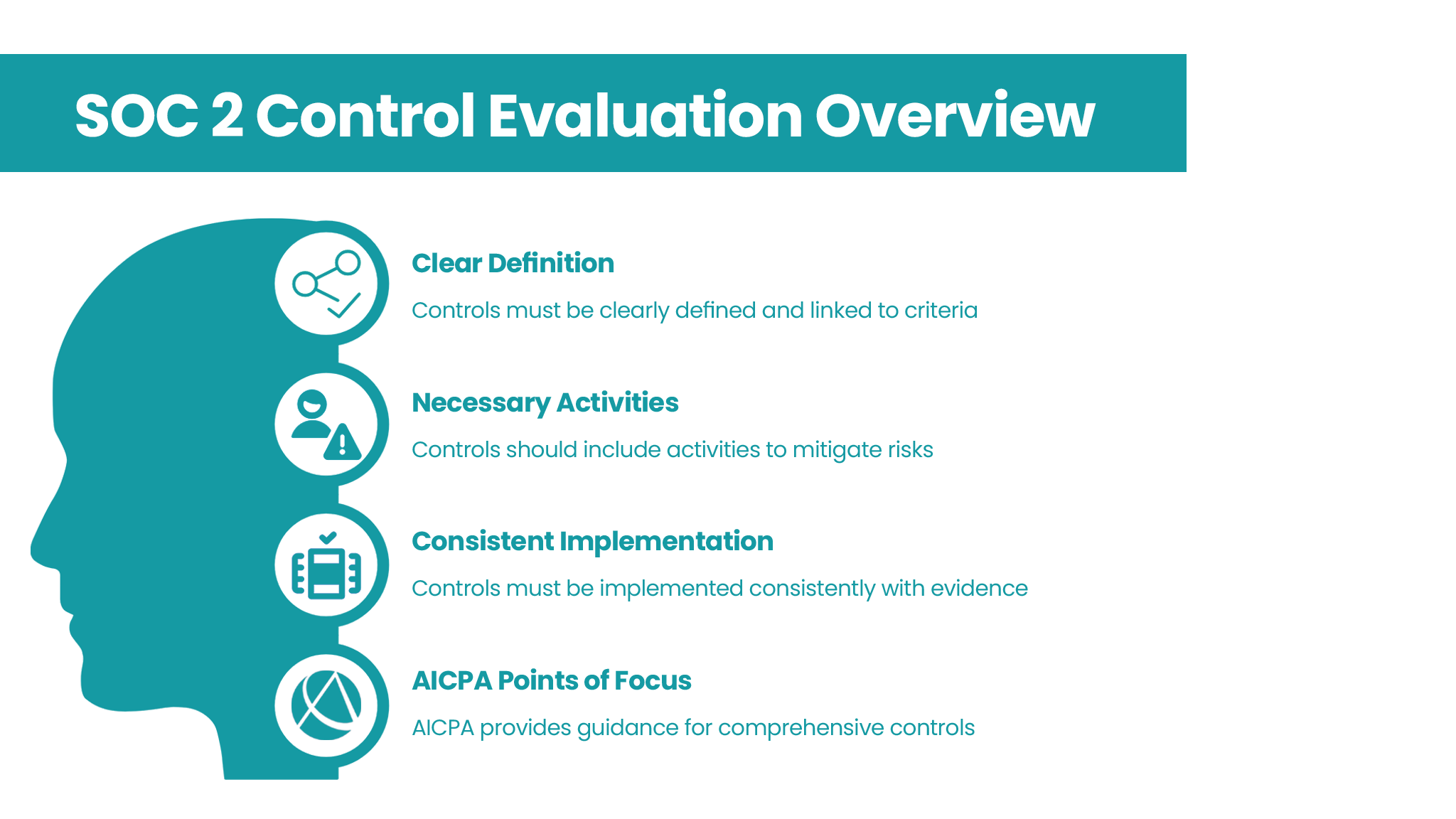
SOC 2 auditors evaluate control descriptions based on their design and operating effectiveness. They want to ensure that each control:
- Is clearly defined and tied to a specific trust services criterion.
- Includes the necessary activities, or technical safeguards to mitigate risks (this is often accomplished across the totality of your internal controls rather than an individual control).
- Is implemented consistently and can be verified through evidence such as access logs, policy documentation, and system monitoring reports.
Auditors also rely on points of focus, which are guidance elements provided by the AICPA to help organizations determine how controls should be designed. These are not mandatory, but they serve as a useful benchmark for ensuring controls are comprehensive and are strongly recommended by the AICPA.
A key challenge organizations face is writing controls that are detailed enough to be meaningful but not so complex that they become difficult to verify. For example, a control stating “System changes undergo a documented peer review process before approval by a senior engineer, with audit logs maintained for compliance verification.” overstates (e.g. “documented” process, and “audit logs”, per above comment) and does include the necessary activity to mitigate risk of unauthorized changes. A better example is “System changes are reviewed and approved by a senior engineer prior to implementation into production.”
Enhance Trust in Your Data Security & Data Integrity
Well-formed control descriptions are essential for a smooth SOC 2 audit and for proving your commitment to data security and integrity. By structuring controls effectively, ensuring consistency with your system description, and aligning with auditor expectations, your organization can avoid unnecessary audit delays and strengthen trust with customers.
If your company is preparing for a SOC 2 audit, Decrypt Compliance can help streamline the process and eliminate administrative overhead. Contact us today to learn how we can be your trusted partner in achieving SOC 2 certification.






