Your clients don’t just want promises; they want proof that their data is safe.
Clients, vendors, and regulators don’t just ask if you’re secure. They ask how you prove it. And in most industries, that proof comes down to recognized frameworks, with ISO 27001 and SOC 2 leading the list.
Global data regulations are tightening. Customers are becoming more risk-aware. According to Gartner, 60% of organizations will face at least one third-party risk management audit or request. Choosing the proper compliance framework isn’t a paperwork exercise — it’s a critical part of your business credibility.
That’s where the ISO 27001 vs SOC 2 differences matter. These two standards are often compared, but they serve different purposes. ISO 27001 focuses on building a structured, organization-wide information security management system. SOC 2, on the other hand, provides externally validated proof of how your systems actually protect customer data.
This blog breaks down both frameworks in a clear, practical way. You’ll understand what each covers, how they differ, when to choose one over the other, and why many businesses choose both.
| Article SummaryISO 27001 is a global certification, while SOC 2 is a U.S.-focused attestation. ISO 27001 builds an internal Information Security Management System (ISMS); SOC 2 evaluates how your systems perform over time. ISO 27001 has a fixed set of 93 controls, whereas SOC 2 allows you to define custom controls based on trust criteria. Licensed CPA firms issue SOC 2 reports, while accredited certifying bodies conduct ISO 27001 certification. Choose ISO 27001 if you require international recognition or a structured, organization-wide security framework. Choose SOC 2 if you’re a U.S.-based SaaS or tech provider needing audit-ready reports for customer trust. |
Understanding ISO 27001 Basics for Business and Compliance Teams
ISO 27001 is an international standard for information security management. It outlines how to create, operate, and improve an Information Security Management System (ISMS). The goal is to protect sensitive data through the implementation of structured policies and controls.
The main objective of ISO 27001 is to help organizations build a system that:
- Identifies and manages security risks.
- Applies necessary controls to reduce those risks.
- Maintains and improves those controls over time.
Components of ISO 27001
- Risk Management
ISO 27001 starts with a risk assessment. Organizations must identify threats to information, assess their impact, and choose how to mitigate them. This makes the system flexible, and controls are based on actual risk, not a checklist.
- Security Controls (Annex A)
There are 93 controls listed in Annex A, grouped under themes like access control, physical security, and incident response. Not all controls are mandatory; organizations choose those that are most relevant. It helps to cover all critical areas of data protection.
- Continual Improvement (PDCA Cycle)
ISO 27001 uses the Plan–Do–Check–Act model:
- Plan: Define security policies and objectives.
- Do: Implement and operate the controls.
- Check: Monitor and review performance.
- Act: Make improvements based on findings.
This helps to ensure that security stays current with evolving threats and business needs.
Moree.
What Does SOC 2 Mean for Your Business Operations?
SOC 2 is a U.S.-based compliance framework designed to help service providers demonstrate that they manage customer data securely and in line with industry expectations. It’s not a certification but an attestation. That means an independent auditor assesses and confirms that your internal systems meet defined security standards.
SOC 2 is built around five Trust Service Criteria:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
Not all five are required; most organizations start with just Security and expand as needed. This flexibility allows companies to tailor SOC 2 to their actual operations and customer expectations.
Types of SOC 2 reports
There are two types of SOC 2 Reports:
- A Type I report checks whether your controls are well-designed at a specific point in time.
- A Type II report looks deeper; it verifies not only that those controls are appropriately designed but also that they are working effectively over a period of time, 6 to 12 months. Clients more commonly request type II because it shows ongoing operational effectiveness.
Licensed CPA firms issue SOC 2 reports after a formal audit. These reports are private; they’re not certifications that can be publicly displayed, like ISO 27001. Instead, you share them under NDA with customers or prospects who ask for proof of your security controls.
Breaking Down ISO 27001 vs SOC 2 Differences for Compliance Teams
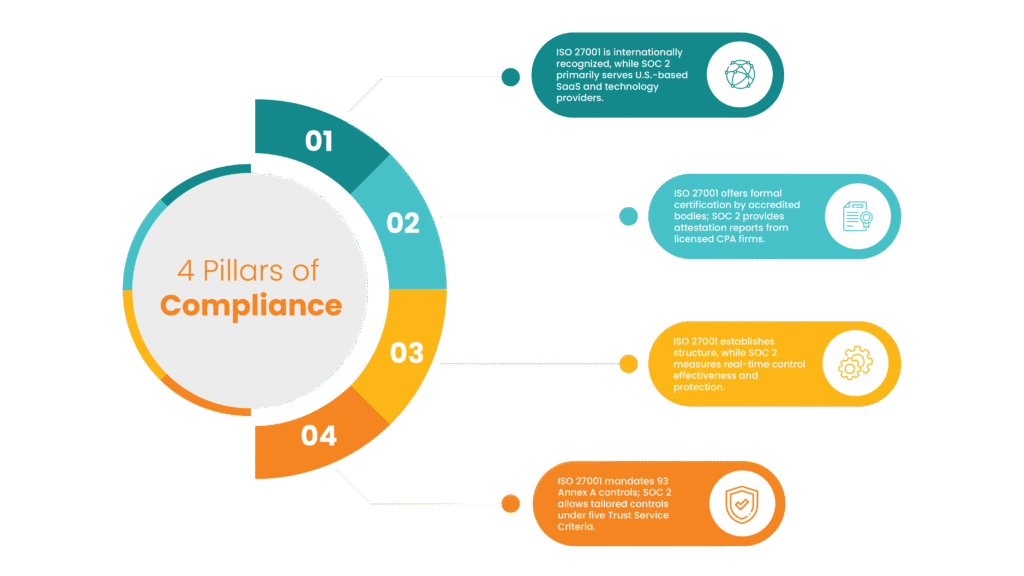
When comparing security frameworks, understanding the differences between ISO 27001 and SOC 2 is essential for selecting the right one for your business’s specific needs. Here’s a breakdown of how they differ under each aspect:
- Origin
ISO 27001 was developed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), making it a globally recognized standard.
SOC 2, on the other hand, was created by the American Institute of Certified Public Accountants (AICPA). It’s more prominent in the U.S. market and widely used by technology and cloud-based service companies.
- Scope
ISO 27001 focuses on an organization-wide Information Security Management System (ISMS). It defines how an organization manages risk, implements policies, and protects all forms of information.
SOC 2 is narrower in scope. It evaluates how a company manages customer data within IT systems and cloud environments, based on specific trust criteria. It’s more control-based than process-driven.
- Certification vs. Attestation
ISO 27001 leads to a formal certification issued by accredited certification bodies after a detailed audit. It confirms that an organization meets the international ISMS standard.
SOC 2 results in an attestation report, not a certificate. A licensed CPA firm conducts the audit and issues a report stating whether the company’s controls meet the AICPA’s trust service criteria.
- Control Set
ISO 27001 includes a defined set of 93 controls listed in Annex A. These cover areas like access control, encryption, and incident response. Organizations select relevant controls based on the level of risk they face.
SOC 2 does not prescribe specific controls. Instead, companies design their own controls that align with the five Trust Service Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
- Report Type
ISO 27001 provides a certificate that organizations can share publicly to demonstrate compliance. It’s valid for three years with periodic surveillance audits.
SOC 2 produces a Type I or Type II report. Type I assesses the design of controls at a single point in time, while Type II evaluates how well those controls operate over several periods of a month.
- Target Audience
ISO 27001 is global and industry-neutral. It’s relevant for any organization handling primarily data, regardless of sector.
SOC 2 is primarily used in the U.S., especially by SaaS companies and data centers on behalf of service providers that store or process customer data for other businesses.
- Flexibility
ISO 27001 takes a risk-based approach, allowing organizations to tailor their ISMS according to their business size, complexity, and threat environment.
SOC 2 offers customized control selection, where companies decide which of the trust principles to include and how to demonstrate compliance. This makes it adaptable but less standardized than ISO 27001.
When Should You Choose ISO 27001 or SOC 2?
If you’re evaluating which framework fits your business better, or whether you may need both, here’s a quick summary of what makes each one the right fit based on your business context and goals:
Choose ISO 27001 if:
- You operate across regions or countries
- You need structured security management across the organization.
- You must meet regulatory requirements, such as GDPR or HIPAA.
- You want a formal certification you can publicly share.
- You believe in continuous improvement.
- You want to embed security into company culture.
Choose SOC 2 if:
- Your clients are primarily U.S.-based
- You need proof that your systems operate securely over time.
- You want flexibility in designing your controls.
- You need private audit reports to share with prospects.
- You’re scaling a B2B SaaS or cloud-based service.
When Does It Make Sense to Implement Both ISO 27001 and SOC 2?
If your organization operates globally or serves a mix of international and locally based clients, pursuing both ISO 27001 and SOC 2 certifications is often a strategic move. Each framework targets a different audience and serves a distinct purpose, which helps broaden your credibility.
ISO 27001 Builds Internal Governance
ISO 27001 helps you establish structured internal processes through an Information Security Management System (ISMS). It covers risk management, policy enforcement, and roles across departments. The focus is on how your business manages information security internally over time.
SOC2 Provides External Assurance
SOC 2, which demonstrates, in hand, an external, independent assessment, effectively showing that your systems and controls are actually working. It’s what clients, especially in the U.S., look for during vendor reviews or onboarding. It translates internal security practices into audit-ready results.
Pursuing both means duplicating your efforts. Many of the controls, such as access management, incident response, and monitoring, overlap. Using control mapping or a crosswalk, you can document and apply a single set of policies that meet both standards. This saves time during implementation and during audits.
If you’re scaling, entering new markets, or facing security requests from both U.S. and international clients, having both frameworks in place helps reduce friction, build trust, and shorten sales cycles. It also prepares you for stricter compliance demands as you grow.
What to Expect When Pursuing SOC 2 and ISO 27001?
Here’s what you can expect during the process of pursuing SOC 2 and ISO 27001, from planning to audit readiness and ongoing compliance.
- Cross-Functional Ownership
These aren’t IT-only frameworks. Security touches HR, legal, engineering, and operations. Expect to coordinate across departments from setting access rules to formalizing onboarding checklists. Both frameworks require alignment beyond the security team.
- Time Investment and Documentation Load
ISO 27001 demands a more structured approach to documentation. You’ll define risk treatment plans, create a Statement of Applicability, and maintain evidence of control implementation. SOC 2 is lightweight, such as process documents, but heavier on operational evidence, including system logs, screenshots, and change management tickets.
- Defined Monitoring Period (SOC 2)
For SOC 2 Type II, you’ll need to operate your controls consistently for a set period (usually 6–12 months). Everything is subject to tracking, alert response times, and incident management processes. ISO 27001 looks at your system readiness at the time of audit, but also evaluates how you manage continuous improvement.
- External Auditor Involvement
SOC 2Licensed CPA firms perform SOC 2 audits. SOC 2 Auditors don’t just check documents; they test how your systems actually behave. Expect requests for live system walkthroughs, historical evidence, and real examples of incidents or access requests.
ISO 2 is focused on being performed by accredited certification bodies, and it is a function that verifies your management system is working as described. At Decrypt Compliance, we conduct both ISO 27001 and SOC 2 audits with a focus on speed, clarity, and accuracy, helping you meet your compliance goals without delays or compromise.
- Ongoing Effort After the Audit
Neither process ends once you “pass.” ISO 27001 requires annual surveillance audits. SOC 2 Type II needs to be renewed regularly. You’ll need to maintain controls, run internal audits, track incidents, and be ready to show improvements each year. The real work is in keeping your systems aligned long after the initial audit.
Faster Certification Starts With the Right Audit Partner
Obtaining ISO 27001 or SOC 2 certification can be a slow and frustrating process. Many companies waste time navigating confusing steps, delays, and back-and-forth communication with auditors, all while trying to grow their business.
At Decrypt Compliance, we make audits simpler and faster. As your independent audit and compliance partner, we help you:
- Streamline SOC 2, ISO 27001, ISO 27701, and ISO 42001 certifications under one coordinated process.
- Identify gaps early and cut through the administrative overhead that slows audits down.
Whether you’re establishing compliance for the first time or renewing multiple frameworks, we ensure you stay audit-ready throughout the year.






