| Article Summary: SOC 2 is a framework that protects customer data and fosters trust. A SOC 2 compliance checklist is a valuable tool for staying organized and audit-ready year-round. Type I and Type II reports show control design and operational effectiveness. Risk assessment, remediation, and evidence collection are key compliance steps. Continuous compliance turns SOC 2 into a driver of growth and credibility. |
Data security has moved from a checkbox to a business-critical expectation. Today’s customers, investors, and partners expect you to prove that their information is safe before they sign a deal. One data breach can cost an average of $4.45M globally and severely damage trust. That’s why SOC 2 has become the minimum bar for SaaS companies and service providers that handle customer data.
Passing a SOC 2 audit once is not enough. Proper compliance is about a continuous effort, maintaining adequate controls, keeping evidence up to date, and managing risks on a year-round basis. Organizations that treat SOC 2 as a “one-time project” often scramble before renewals, face audit exceptions, or worse, leave gaps that could lead to real security incidents.
This blog provides a practical SOC 2 compliance checklist to help you stay audit-ready, reduce risk, and leverage compliance as a business advantage. While the term “SOC 2 compliance” is often used informally across the industry, it’s important to note that SOC 2 is an attestation framework, not a compliance certification.
What Is SOC 2 Compliance?
SOC 2, short for System and Organization Controls 2, is a widely recognized framework developed by the American Institute of Certified Public Accountants (AICPA). SOC 2 Trust Services Criteria is essentially a set of criteria for a company’s attestation, rather than a standard to comply with. It is designed to evaluate how organizations manage and protect customer data. Rather than being a rigid, one-size-fits-all certification, SOC 2 offers a flexible framework that organizations can adapt to their unique systems, processes, and risks.
At its core, SOC 2 compliance focuses on the five Trust Services Criteria (TSC):
- Security: Protecting systems and data against unauthorized access.
- Availability: Ensuring systems are operational and accessible as promised.
- Confidentiality: Protecting sensitive information from unauthorized disclosure.
- Processing Integrity: Guaranteeing that system processing is complete, valid, accurate, and timely.
- Privacy: Protecting personal information according to privacy principles.
For many B2B SaaS companies, cloud service providers, and other organizations handling sensitive customer data, SOC 2 compliance has become a minimum expectation. Achieving SOC 2 compliance indicates that your organization has robust security practices, well-documented controls, and a commitment to safeguarding customer data.
Beyond meeting audit requirements, SOC 2 compliance offers real business value. It helps build trust with clients, simplifies vendor security reviews, and gives you a competitive edge when pursuing enterprise customers who demand proof of robust security measures.
Why a SOC 2 Compliance Checklist Is Essential for Your Business?
Implementing a SOC 2 compliance checklist helps you stay ahead of compliance tasks, protect customer data, and build trust. Here is why every modern business needs a SOC 2 Compliance checklist:
- Provides Comprehensive Coverage
A SOC 2 checklist ensures you don’t overlook any requirement, from policies and procedures to technical controls and evidence collection. It acts as a roadmap that guides you through every step of compliance, so you stay aligned with the Trust Services Criteria year-round.
- Simplifies Audit Readiness
Instead of scrambling right before your next audit, a checklist keeps you organized and ready at all times. It helps you document controls, track tasks, and gather evidence proactively, making the entire audit process smoother and less stressful.
- Demonstrates Your Commitment to Security
Customers, partners, and prospects want to know that you take data security seriously. Following a SOC 2 checklist shows that you have a structured approach to safeguarding their information, which builds confidence and trust in your business.
- Improves Vendor and Third-Party Management
SOC 2 compliance often includes monitoring vendors and their security practices. A checklist ensures that you regularly review vendor SOC reports, request bridge letters, and validate their controls, keeping your entire supply chain secure.
SOC 2 Compliance Checklist: What Every Business Should Follow
Below is a SOC 2 compliance checklist designed to help you define your scope, fix gaps early, and stay audit-ready, whether it’s your first SOC 2 certification or your next renewal.
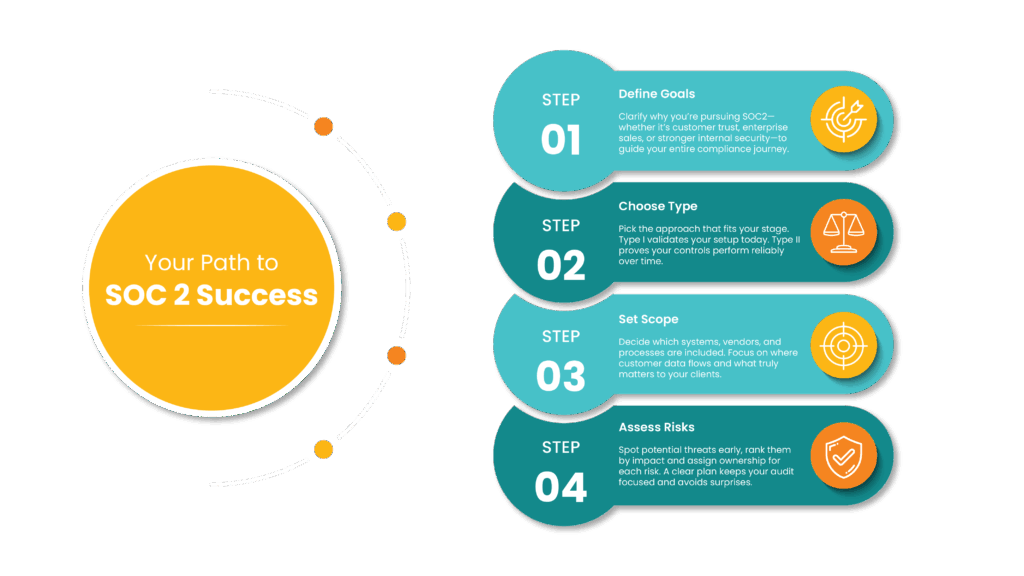
- Define Your Compliance Goals
Before you dive in, get clear on why you’re pursuing SOC 2. Are you doing it to meet customer requirements, gain a competitive edge in enterprise sales, or enhance internal security maturity?
Defining your goals upfront helps shape the rest of the process, including which Trust Services Criteria (TSC) you include beyond the required Security category.
- Decide Between SOC 2 Type I or Type II
Not every business needs the same level of audit.
- Type I: Validates that your controls are appropriately created at a single point in time, a good first step if you’ve never been through SOC 2 before.
- Type II: Tests that your controls are working effectively over a set observation period (usually 3–12 months), better for organizations ready to demonstrate long-term consistency.
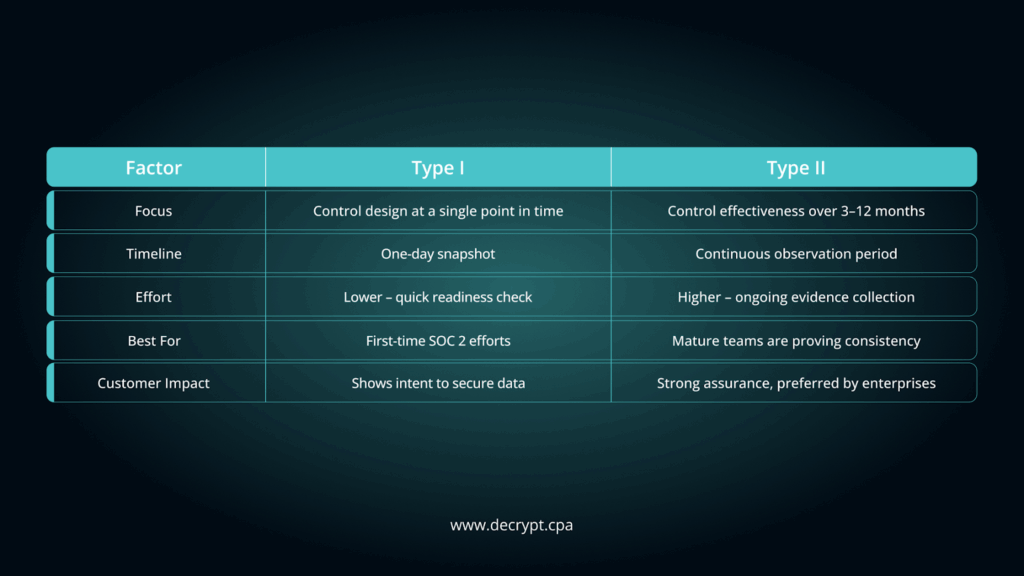
Select the report type that aligns with your current maturity and your customers’ expectations.
- Map Out Your Scope
Figure out which systems, processes, and vendors will be covered by your SOC 2 report.
Focus on where customer data is stored, processed, or transmitted. Exclude systems that are not relevant; narrowing the scope keeps the effort manageable. Document the boundaries clearly with system descriptions and architecture diagrams.
For instance, if your customers care deeply about uptime and worry about service interruptions, it makes sense to include Availability to show that you monitor and manage system reliability.
Similarly, suppose your platform collects or stores personal information (such as healthcare data, birthdays, or social security numbers). In that case, adding Privacy ensures that your handling of personally identifiable information (PII) meets strict standards.
- Identify and Prioritize Risks
Before implementing or updating controls, perform a risk review. List potential threats to your systems (unauthorized access, data loss, downtime). Rank them based on likelihood and impact.
Assign ownership so every risk has a clear point of accountability.
- Spot Gaps and Plan Remediation
Compare your current state against SOC 2 requirements. Identify missing policies, weak controls, or gaps in monitoring and control. Build a step-by-step plan to fix those gaps by assigning tasks, owners, and deadlines. Keep a record of progress for future audits.
- Put Your Controls Into Action
With the identified gaps in place, roll out the required policies and technical controls.
Formalize processes like access reviews, change management, incident response, and vendor oversight.
Implement security measures like MFA, encryption, logging, and patching schedules. Test the controls internally to ensure they function as intended and produce evidence that can be shared.
- Run a Readiness Review
Think of this as a “practice audit.” Review the evidence you’ve collected so far. Check that all policies are approved, communicated, and followed by your team. Address any issues discovered so you go into the real audit prepared.
- Choose Your Auditor
Select a reputable CPA firm with experience in SOC 2 and knowledge of your industry.
Align on the timeline, scope, and reporting deadlines. Ensure that your internal stakeholders are aware of the expectations placed on them during the engagement.
- Complete the SOC 2 Audit
Finally, go through the audit process itself. Provide documentation and evidence securely.
Participate in walkthroughs and answer questions clearly and concisely. Review the draft report before it’s finalized to ensure accuracy. Once complete, share the report with customers and prospects to build trust.
Strengthen Customer Trust with SOC 2 Audits
Preparing for SOC 2 can be time-consuming and complex, especially as audit cycles repeat and expectations evolve. At Decrypt Compliance, we provide independent SOC 2 audits, giving your stakeholders the assurance they need, without adding unnecessary operational burden.
Decrypt Compliance serves as your independent audit partner, ensuring objectivity, clarity, and professionalism throughout the process.
If you’re ready to demonstrate trust, transparency, and security to your customers, without losing momentum, our audit team is here to help.






